Sometimes the special character (i-e soh and eot) may appear in data and as a part of data
they will be misinterpreted as framing data.
The solution to this problem is Byte stuffing.
In general to distinguish between data being sent and control information such as
frame delimiters network systems arrange for the sending side to change the data slightly
before it is sent because systems usually insert data or bytes to change data for
transmission, the technique is known as Data Stuffing.
There are two types of data stuffing:
• Byte Stuffing
• Bit Stuffing
Byte stuffing refers stuffing with character oriented hardware and bit stuffing
refers to bit oriented hardware.
Byte stuffing translates each reserved byte into two unreserved bytes. For
example: it can use esc as prefix followed by x for soh, y for eot and z for eco.
The receiver then replaces each occurrence of esc x, esc y and esc z by the
corresponding single character. This is shown in figure below:
Archives
-
▼
2010
(31)
-
▼
January
(18)
- BYTE STUFFING
- Design Recipe
- Critical Skills
- Alan Perlis
- Program
- UNIVAC 1 1951
- Floppy Disk 1950
- PACKETS AND FRAMES
- PACKETS, FRAMES AND ERROR DETECTION
- C language program Lecture 3
- Layout Design & Architectural Simulations
- Room Layout Design and Architectural Simulations
- Transistor – 1947
- ENIAC – 1946
- Harvard Mark 1 – 1943:
- ABC – 1939
- Vacuum Tube – 1904
- C language program Lecture 2
-
▼
January
(18)
Partner Link
Cheap Mobile Phones
- Cheap Mobile Phones - Best Mobile Phone Deals, Laptops, Sat Nav Devices, Cordless Phones, Internet Phones, Broadband Internet Deals from leading retailers of UK. Choose Products and Compare Prices for best deals.
Mobile Phones
- Offers mobile phones on contract,
pay as you go, sim free deals with free gifts.
We compare latest phone deals from
leading retailers of UK.
. ||
Custom logo design
Get your company a logo design. Professional logo designs by expert logo designers. Call 0208 133 2514 for custom logo design packages.
Top Site
BYTE STUFFING
Labels: Computer Networks
Design Recipe
To design a program properly, we must:
- Analyze a problem statement, typically expressed as a word problem
- Express its essence, abstractly and with examples
- Formulate statements and comments in a precise language
- Evaluate and revise the activities in light of checks and tests
- These skills are useful for anybody
- All assignments in this course should follow the these guidelines
Alan Perlis
“It goes against the grain of modern
education to teach children to program.
What fun is there in making plans,
acquiring discipline in organizing
thoughts, devoting attention to detail
and learning to be self-critical? “
UNIVAC 1 1951
UNIVAC-1. The first commercially successful electronic computer, UNIVAC I, was
also the first general purpose computer - designed to handle both numeric and textual
information. It was designed by J. Presper Eckert and John Mauchly. The
implementation of this machine marked the real beginning of the computer era.
Remington Rand delivered the first UNIVAC machine to the U.S. Bureau of Census in
1951. This machine used magnetic tape for input.
first successful commercial computer
design was derived from the ENIAC (same developers)
first client = U.S. Bureau of the Census
$1 million
48 systems built
Labels: Introduction to Computing
Floppy Disk 1950
Invented at the Imperial University in Tokyo by Yoshiro Nakamats
Labels: Introduction to Computing
PACKETS AND FRAMES
PACKETS:
Packet is a generic term that refers to small block of data. Packet have different
format. Each hardware uses different packet format.
FRAME:
A frame or hardware frame denotes a packet of a specific format on a specific
hardware technology.
FRAME FORMAT:
We need to define a standard format for data to indicate the beginning and end of
the frame. Header and tail are used to frame the data as shown in the figure below.
We see that in the figure soh and eot are used to denote the start of header and end of tail.
FRAMING IN PRACTICE:
In practice there is a disadvantage of overhead. To avoid the no delay between
two frames each frame sends an extra character between block of data.
The framing in practice also has some transmission problems just like:
- Missing eot indicates sending computer crashed.
- Missing soh indicates receiving computer missed beginning of message.
- Bad frame is discarded
Labels: Computer Networks
PACKETS, FRAMES AND ERROR DETECTION
INTRODUCTION:
The previous chapters of data communication described how bits are transmitted
across a physical network using a transmission medium.
This chapter introduces the concept of packets of data rather than bits for
communication.
CONCEPT OF ‘PACKET’:
Network systems divide data in small blocks or junks called packets, which they
send individually. Why we need packets rather than bits? The answer to this question is
because a sender and receiver need to coordinate to detect transmission errors. Also the
individual connection between each pair of computers is not possible. That’s why to
solve these problems shard network connections are made among many workstations.
PROBLEMS WITH SHARING:
The demand of sharing is very high because many computers need to use the shared
networks. In addition to this some applications have large data transfer. In this way they
hold the network for long time. But on the other hand some applications cannot wait so
long. So we need a mechanism for fairness.
SOLUTION FOR FAIRNESS:
To the fairness, the solution is to divide the data into small block or chunks called
‘PACKETS’. Computers take turns to send one packet at a time over the shared
connection.
Because each packet is small so no computer experiences a long delay.
Example:
In the figure one reason for using the packets is illustrated. We see that in a shared
resource when one pair of computer communicates, the other must wait. To understand
the use of packet here, let’s suppose a transmission with packets in the figure.
WITHOUT PACKETS:
A 5MB file transferred across network with 56Kpbs capacity will require 12 minutes.
This means that all that computers will be forced to wait for 12 minutes before initiating
entire file) has been sent.
Suppose file is broken into 1000 byte packets.
Now each packet takes less than 0.2 seconds to transmit. Here other computers must only

Note: - if both files are 5MB long, each now takes 24 minutes to transmit. But if the
second file is 10MB long it sill be transmitted in only 2.8 seconds while 5MB file still
takes roughly 12 minutes.
PACKETS AND TDM:
Dividing data into small packets allow time division multiplexing. In TDM each packet
leaves the source and is switched on the shared communication channel through a
multiplexer. At the destination the packet is switched through a demultiplexer to the
destination.
In the figure this process is illustrated with a multiplexing circuit shown.
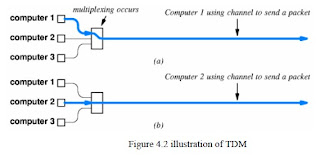
Labels: Computer Networks
C language program Lecture 3
This same task can be performed by the following program as well. In this case the video text memory is accessed byte by byte.
unsigned char far *scr=(unsigned char far*)0xb8000000;
void main()
{
*scr=0x56;
*(scr+1)=0x07;
*(scr+2)=0x55;
*(scr+3)=0x70;
}
The next example fills whole of the screen with spaces. This will clear the contents of the screen.
unsigned char far *scr=(unsigned char far*)0xb8000000; //corrected
void main()
{
int i; //instruction added
for (i=0;i<2000;i++) scr="0x20;" scr="scr+2;">void interrup
void interrupt newfunc();
char far *scr=(char far* ) 0xb8000000;
void main()
{
setvect(0x08,newfunc);
}
void interrupt newfunc ()
{
*scr=0x41; //corrected
*(scr+1)=0x07; //corrected
In the above example the timer interrupt is intercepted such that whenever the timer interrupt is invoked (by means of hardware) the memory resident newfunc() is invoked. This function simply displays the ASCII character 0x41 or ‘
Here is another example.
void interrupt (*old)();
void interrupt newfunc();
char far *scr=(char far* ) 0xb8000000;
void main( )
{
old=getvect(0x08);
setvect(0x08,newfunc); //corrected
}
void interrupt newfunc ( )
{
*(scr+j)=‘9’; }
}
(*old)();
}
This program scans through all the bytes of text display memory when int 8 occurs. It once resident will replace all the ‘1’ on the screen by ‘9
The keyboard Interrupt
Keyboard is a hardware device and it makes use of interrupt number 9 for its input operations. Whenever a key is pressed interrupt # 9 occurs. The operating system processes this interrupt in order to process the key pressed. This interrupt usually reads the scan code from the keyboard port and converts it into the appr Lets now experiment on the keyboard interrupt to understand its behavior
Lets now experiment on the keyboard interrupt to understand its behavior
Example
#include
void interrupt newfunc( );
void main( )
{
old = getvect(0x09);
keep(0,1000);
}
void interrupt newfunc ( )
{
(*old)( );
(*old)( );
}
This program simply intercepts the keyboard interrupt and places the address of newint in the IVT. The newint simply invokes the origin
Example
#include
void interrupt (*old)( );
void interrupt newfunc( );
void main( )
{
old = getvect(0x09);
setvect(0x09,newfunc);
}
void interrupt newfunc ( )
{
*scr = 64;
(*old)( );
}
The above program is quite familiar it will just set the caps lock status whenever a key is pressed. In this case the keyboard interrup
Example
void interrupt (*old)( );
void interrupt newfunc( );
char far *scr = (char far* ) 0xB8000000;
void main( )
{
old = getvect(0x09);
setvect(0x09,newfunc);
keep(0,1000);
}
void interrupt newfunc ( )
{ for( j = 0;j <>
void interrupt (*oldTimer)( ); //corrected
void interrupt (*oldKey)( ); //corrected
void interrupt newTimer ( );
void interrupt newKey ( );
char far *scr = (char far* ) 0xB8000000
int i, t = 0, m = 0;
char charscr [4000];
void main( )
{
oldTimer = getvect(8);
oldKey = getvect (9);
setvect (8,newTimer);
setvect (9,newKey);
getch();
getch();
getch();
}
void interrupt newTimer ( )
{
t++;
if ((t >= 182) && (m == 0))
{
In the above example the function Proc1() is invoked. On invocation the register AX contained the value 1234H, the code within the function Proc1() changes the value in AX to FF55H. On return AX will contain the value 1234H if the function have been implemented as a reentrant procedure i.e a reentrant procedure would restore the values in registers their previous value (saved in the stacked) before returning.
C language reentrant procedures save the registers in stack following the order AX, BX, CX, DX, ES, DS, SI, DI, BP on invocation and restores in reverse order before return.
This fact about reentrant procedures can be analysed through following example.
#include
void interrupt *old();
void interrupt newint()
void main ()
{
old = getvect(0x65);
setvect(0x65,newint);
_AX=0xf00f;
geninterrupt(0x65);
a = _AX
printf(“%x”,a);
}
void interrupt newint()
{
_AX=0x1234;
}
Firstly its important to compile this above and all the rest of the examples as .C files and not as .CPP file. It these codes are compiled using .CPP extension then there is no surety that this program could be compiled.
Again int 65H is used for this experiment. The int 65H vector is made to point at the function newint(). Before calling the interrupt 65H value 0xF00F is placed in the AX register. After invocation of int 65H the value of AX register is changed to 0x1234. But after return if the value of AX is checked it will not be 0x1234 rather it will be 0xF00F indicating that the values in registers are saved on invocation and restore before return and also that the interrupt type procedures are reentrant.
Labels: Systems Programming
Transistor – 1947
The first transistor was invented at Bell Laboratories on December 16, 1947 by William
Shockley. This was perhaps the most important electronics event of the 20th century, as
it later made possible the integrated circuit and microprocessor that are the basis of
modern electronics. Prior to the transistor the only alternative to its current regulation
and switching functions (TRANSfer resISTOR) was the vacuum tubes, which could only
be miniaturized to a certain extent, and wasted a lot of energy in the form of heat.
Compared to vacuum tubes, it offered:
smaller size
better reliability
lower power consumption
lower cost
Labels: Introduction to Computing
ENIAC – 1946
ENIAC I (Electrical Numerical Integrator And Calculator). The U.S. military sponsored
their research; they needed a calculating device for writing artillery-firing tables (the
settings used for different weapons under varied conditions for target accuracy).
John Mauchly was the chief consultant and J Presper Eckert was the chief engineer.
Eckert was a graduate student studying at the Moore School when he met John Mauchly
in 1943. It took the team about one year to design the ENIAC and 18 months and
500,000 tax dollars to build it.
The ENIAC contained 17,468 vacuum tubes, along with 70,000 resistors and 10,000
capacitors.
Labels: Introduction to Computing
Harvard Mark 1 – 1943:
Howard Aiken and Grace Hopper designed the MARK series of computers at Harvard
University. The MARK series of computers began with the Mark I in 1944. Imagine a
giant roomful of noisy, clicking metal parts, 55 feet long and 8 feet high. The 5-ton
device contained almost 760,000 separate pieces. Used by the US Navy for gunnery and
ballistic calculations, the Mark I was in operation until 1959.
The computer, controlled by pre-punched paper tape, could carry out addition,
subtraction, multiplication, division and reference to previous results. It had special
subroutines for logarithms and trigonometric functions and used 23 decimal place
numbers. Data was stored and counted mechanically using 3000 decimal storage wheels,
1400 rotary dial switches, and 500 miles of wire. Its electromagnetic relays classified the
machine as a relay computer. All output was displayed on an electric typewriter. By
today's standards, the Mark I was slow, requiring 3-5 seconds for a multiplication
operation
Labels: Introduction to Computing
ABC – 1939
The Atanasoff-Berry Computer was the world's first electronic digital computer. It was
built by John Vincent Atanasoff and Clifford Berry at Iowa State University during 1937-
42. It incorporated several major innovations in computing including the use of binary
arithmetic, regenerative memory, parallel processing, and separation of memory and
computing functions
Labels: Introduction to Computing
Vacuum Tube – 1904
A vacuum tube is just that: a glass tube surrounding a vacuum (an area from which all
gases has been removed). What makes it interesting is that when electrical contacts are
put on the ends, you can get a current to flow though that vacuum.
A British scientist named John A. Fleming made a vacuum tube known today as a diode.
Then the diode was known as a "valve,"
Labels: Introduction to Computing
C language program Lecture 2
Another Example:
#include
void interrupt (*oldint65)( );
setvect(0x65, newint65);
if (( _AH ) == 0) //corrected
{
{
if (( _AH ) == 1) //corrected
}
Various interrupts provide a number of services. The service number is usually placed in the AH register before invoking the interrupt. The ISR should in turn check the value in AH register and then perform the function accordingly. The above example exemplifies just that. In this example int 65 is assigned two services 0 and 1. Service 0 prints the string st and service 1 prints the string st1. These services can be invoked in the following manner.
void main()
{ Fig 2 (The original ISR being called at he end of new routine)
Fig 2 (The original ISR being called at he end of new routine)  Fig 3 (The original ISR invoked at the start of new ISR)
Fig 3 (The original ISR invoked at the start of new ISR) Care must be taken while invoking the original interrupt. Generally in case hardware interrupts are intercepted invoking the original interrupt at the start of new routine might cause some problems whereas in case of software interrupts the original interrupt can be invoked anywhere
Care must be taken while invoking the original interrupt. Generally in case hardware interrupts are intercepted invoking the original interrupt at the start of new routine might cause some problems whereas in case of software interrupts the original interrupt can be invoked anywhere
Sample Program for interrupt Interception
void interrupt newint();
void interrupt (*old)();
void main()
{
old=getvect(0x08);
setvect(0x08,newint);
keep(0,1000);
}
void interrupt newint ()
{
…
…
(*old)();
}
The above program gets the address stored at the vector of interrupt 8 and stores it in the pointer oldint. The address of the interrupt function newint is then placed at the vector of int 8 and the program is made memory resident. From this point onwards whenever interrupt 8 occurs the interrupt function newint is invoked. This function after performing its operation calls the original interrupt 8 whose address has been stored in oldint pointer.
Timer Interrupt
In the coming few examples we will intercept interrupt 8. This is the timer interrupt. The timer interrupt has following properties.
- Its an Hardware Interrupts
- It is Invoked by Means of Hardware
- It approximately occurs 18.2 times every second by means of hardware.
BIOS Data Area
BIOS contains trivial I/O routines which have been programmed into a ROM type device and is interfaced with the processor as a part of main memory. However the BIOS routines would require a few variables, these variables are stored in the BIOS data arera at the location 0040:0000H in the main memory.
One such byte stored in the BIOS data area is the keyboard status byte at the location 40:17H. This contains the status of various keys like alt, shift, caps lock etc. This byte can be described by the diagram below
Fig 4 (Keyboard status byte)

Another Example
#include
void interrupt (*old)();
void main()
old=getvect(0x08);
setvect(0x08,new);
}
*scr=64;
(*old)();
This fairly simple example intercepts the timer interrupt such that whenever the timer interrupt occurs the function new() is invoked. Remember this is .C program and not a .CPP program. Save the code file with .C extension after writing this code
Memory Mapped I/O and Isolated I/O

Fig 6 (Memory mapped I/O)

Memory Mapped I/O on Monitor
One of the devices in standard PCs that perform memory mapped I/O is the display device (Monitor). The output on the monitor is controller by a controller called video controller within the PC. One of the reason for adopting memory mapped I/O for the monitor is that a large amount of data is needed to be conveyed to the video controller in order to describe the text or that graphics that is to be displayed. Such large amount of data being output through isolated I/O does not form into a feasible idea as the number of port in PCs is limited to 65536.
The memory area starting from the address b800:0000H. Two bytes (a word) are reserved for a single character to be displayed in this area. The low byte contains the ASCII code of the character to be displayed and the high byte contains the attribute of the character to be displayed. The address b800:0000h corresponds to the character displayed at the top left corner of the screen, the next word b800:0002 corresponds to the next character on the same row of the text screen and so on as described In the diagram below.
Fig 7 (Memory mapped I/O on monitor)

The attribute byte (higher byte) describes the forecolor and the backcolor in which the character will be displayed. The DOS screen carries black as the backcolor and white as the fore color by default. The lower 4 bits (lower nibble) represents the forecolor and the higher 4 bits (higher nibble) represents the back color as described by the diagram below
Fig 8 (Attribute Byte)
 To understand all describe above lets take a look at this example.
To understand all describe above lets take a look at this example.unsigned int far *scr=0xb8000000;
void main()
{
(*scr)=0x0756;
(*(scr+1))=0x7055;
}
This example will generate the output VU
The far pointer scr is assigned the value 0xb800H in the high word which is the segment address and value 0x0000H in the low word which is the offset address. The word at this address is loaded with the value 0x0756H and the next word is loaded by the value 0x7055H, 0x07 is the attribute byte meaning black back color and white fore color and the byte 0x70h means white back color and black fore color. ).0x56 and 0x55 are the ASCII value of “V” and “U” respectively.
Labels: Systems Programming







