* A complete guide to wireless communication technology to network professionals, and telecommunications. * Easy to use training reference data communications and wireless technology students to get an overall picture of WLAN, WPAN, WMAN, WWAN and Mobile technologies. * A unique marketing tool for telecom and wireless hardware, software and service providers, lead generation, and a unique gift for partners and customers. * Protocol stack information on the WLAN, WiMAX, Bluetooth, ZigBee, UWB and wireless. * Graphs, trees in developing technologies and a wireless G 4G and GSM / GPRS / WCDMA and cdmaOne/CDMA2000. * Comprehensive reference architecture framework to show all wireless technologies in a chart for quick understanding of the framework. * Designed for experts who have decades of experience in wireless, data and telecommunications.
Designed for wireless communication engineers and marketing, wireless communication technology educators and students, this card's wireless communication technology covers all major wireless technologies: Wireless LAN (WLAN), WiMAX for metropolitan area networks (WMAN), Bluetooth, ZigBee and UWB for personal area network (WPAN) and mobile wireless technologies (WWAN) from 1G to 3G. The wireless hardware, software and service providers can buy as a marketing, sales, trade shows, seminars and web / email leads generation programs. Telecom networks and IT training organizations can use it as an additional tool of education or a gift for motivating students and trainees
Archives
-
▼
2010
(31)
-
►
January
(18)
- BYTE STUFFING
- Design Recipe
- Critical Skills
- Alan Perlis
- Program
- UNIVAC 1 1951
- Floppy Disk 1950
- PACKETS AND FRAMES
- PACKETS, FRAMES AND ERROR DETECTION
- C language program Lecture 3
- Layout Design & Architectural Simulations
- Room Layout Design and Architectural Simulations
- Transistor – 1947
- ENIAC – 1946
- Harvard Mark 1 – 1943:
- ABC – 1939
- Vacuum Tube – 1904
- C language program Lecture 2
-
►
January
(18)
Partner Link
Cheap Mobile Phones
- Cheap Mobile Phones - Best Mobile Phone Deals, Laptops, Sat Nav Devices, Cordless Phones, Internet Phones, Broadband Internet Deals from leading retailers of UK. Choose Products and Compare Prices for best deals.
Mobile Phones
- Offers mobile phones on contract,
pay as you go, sim free deals with free gifts.
We compare latest phone deals from
leading retailers of UK.
. ||
Custom logo design
Get your company a logo design. Professional logo designs by expert logo designers. Call 0208 133 2514 for custom logo design packages.
Top Site
Wireless Communications Technology Map Poster
Labels: Wireless Technology Map
APP Server
APP Server is a tool that allows users to meet the challenges password token received from an external network access server (NAS). Access servers network provides a complex security algorithm that forces a user to be in possession of a security card that can generate a password. When a user on the LAN will start a program that requires a connection to a host on a secure network, Pipeline is calling, and after negotiating the initial session, a remote NAS challenge going back. The user has 60 seconds to obtain and enter the password of the current dynamic security card.
Labels: APP Server
What Programming Actually Is
This article outlines what programming actually is, with a view to helping aspiring programmers decide if they are making the right career choice.
List data structure
This is a new data structure for you. The List data structure is among the most generic of data structures. In daily life, we use shopping list, groceries list, list of people to invite to a dinner, list of presents to give etc. In this course, we will see how we use lists in programming.
A list is the collection of items of the same type (grocery items, integers, names). The data in arrays are also of same type. When we say int x[6]; it means that only the integers can be stored in it. The same is true for list. The data which we store in list should be of same nature. The items, or elements of the list, are stored in some particular order. What does this mean? Suppose in the list, you have the fruit first which are also in some order. You may have names in some alphabetical order i.e. the names which starts with A should come first followed by the name starting with B and so on. The order will be reserved when you enter data in the list.
It is possible to insert new elements at various positions in the list and remove any element of the list. You have done the same thing while dealing with arrays. You enter the data in the array, delete data from the array. Sometimes the array size grows and at times, it is reduced. We will do this with the lists too.
List is a set of elements in a linear order. Suppose we have four names a1, a2, a3, a4 and their order is as (a3, a1, a2, a4) i.e. a3, is the first element, a1 is the second element, and so on. We want to maintain that order in the list when data is stored in the list. We don’t want to disturb this order. The order is important here; this is not just a random collection of elements but an ordered one. Sometimes, this order is due to sorting i.e. the things that start with A come first. At occasions, the order may be due to the importance of the data items. We will discuss this in detail while dealing with the examples.
Now we will see what kind of operations a programmer performs with a list data structure. Following long list of operations may help you understand the things in a comprehensive manner.
 createList() is a function which creates a new list. For example to create an array, we use int x[6] or int* y = new int[20]; we need similar functionality in lists too. The copy() function will create a copy of a list. The function clear() will remove all the elements from a list. We want to insert a new element in the list, we also have to tell where to put it in the list. For this purpose insert(X, position) function is used. Similarly the function remove(position) will remove the element at position. To get an element from the list get(position) function is used which will return the element at position. To replace an element in the list at some position the function update(X, position) is used. The function find(X) will search X in the list. The function length() tells us about the number of elements in the list.
createList() is a function which creates a new list. For example to create an array, we use int x[6] or int* y = new int[20]; we need similar functionality in lists too. The copy() function will create a copy of a list. The function clear() will remove all the elements from a list. We want to insert a new element in the list, we also have to tell where to put it in the list. For this purpose insert(X, position) function is used. Similarly the function remove(position) will remove the element at position. To get an element from the list get(position) function is used which will return the element at position. To replace an element in the list at some position the function update(X, position) is used. The function find(X) will search X in the list. The function length() tells us about the number of elements in the list.
We need to know what is meant by “particular position” we have used “?” for this in the above table. There are two possibilities:
- Use the actual index of element: i.e. insert it after element 3, get element number 6. This approach is used with arrays
- Use a “current” marker or pointer to refer to a particular position in the list.
If we use the “current” marker, the following four methods would be useful:
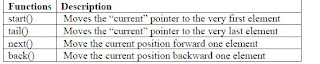 In the next lecture, we will discuss the implementation of the list data structure and write the functions discussed today, in C++ language.
In the next lecture, we will discuss the implementation of the list data structure and write the functions discussed today, in C++ language.
Labels: Data Structures
Why Programming is important
The question most of the people ask is why should we learn to program when there are so many application software and code generators available to do the task for us. Well the answer is as give by the Matthias Felleisen in the book ‘How to design programs’
“The answer consists of two parts. First, it is indeed true that traditional forms of programming are useful for just a few people. But, programming as we the authors understand it is useful for everyone: the administrative secretary who uses spreadsheets as well as the high-tech programmer. In other words, we have a broader notion of programming in mind than the traditional one. We explain our notion in a moment. Second, we teach our idea of programming with a technology that is based on the principle of minimal intrusion. Hence, our notion of programming teaches problem-analysis and problem-solving skills without imposing the overhead of traditional programming notations and tools.”
Hence learning to program is important because it develops analytical and problem solving abilities. It is a creative activity and provides us a mean to express abstract ideas. Thus programming is fun and is much more than a vocational skill. By designing programs, we learn many skills that are important for all professions. These skills can be summarized as:
- Critical reading
- Analytical thinking
- Creative synthesis
Arrays
You have already studied about arrays and are well-versed with the techniques to utilize these data structures. Here we will discuss how arrays can be used to solve computer problems. Consider the following program:
main( int argc, char** argv )
{
int x[6];
int j;
for(j = 0; j < 6; j++)
x[j] = 2 * j;
}
We have declared an int array of six elements and initialized it in the loop.
Let’s revise some of the array concepts. The declaration of array is as int x[6]; or float x[6]; or double x[6]; You have already done these in your programming assignments. An array is collection of cells of the same type. In the above program, we have array x of type int of six elements. We can only store integers in this array. We cannot put int in first location, float in second location and double in third location. What is x? x is a name of collection of items. Its individual items are numbered from zero to one less than array size. To access a cell, use the array name and an index as under:
x[0], x[1], x[2], x[3], x[4], x[5]
To manipulate the first element, we will use the index zero as x[0] and so on. The arrays look like in the memory as follows:
Array occupies contiguous memory area in the computer. In case of the above example, if some location is assigned to x[0], the next location can not contain data other than x[1]. The computer memory can be thought of as an array. It is a very big array. Suppose a computer has memory of 2MB, you can think it as an array of size 2 million and the size of each item is 32 bits. You will study in detail about it in the computer organization, and Assembly language courses. In this array, we will put our programs, data and other things.
In the above program, we have declared an array named x. ‘x’ is an array’s name but there is no variable x. ‘x’ is not an lvalue. If some variable can be written on the left- hand side of an assignment statement, this is lvalue variable. It means it has some memory associated with it and some value can be assigned to it. For example, if we have the code int a, b; it can be written as b = 2; it means that put 2 in the memory location named b. We can also write as a = b; it means whatever b has assign it to a, that is a copy operation. If we write as a = 5; it means put the number 5 in the memory location which is named as a. But we cannot write 2 = a; that is to put at number 2 what ever the value of a is. Why can’t we do that? Number 2 is a constant. If we allow assignment to constants what will happen? Suppose ‘a’ has the value number 3. Now we assigned number 2 the number 3 i.e. all the number 2 will become number 3 and the result of 2 + 2 will become 6. Therefore it is not allowed.
‘x’ is a name of array and not an lvalue. So it cannot be used on the left hand side in an assignment statement. Consider the following statements
int x[6];
int n;
x[0] = 5; x[1] = 2;
x = 3; //not allowed
x = a + b; // not allowed
x = &n; // not allowed
In the above code snippet, we have declared an array x of int. Now we can assign values to the elements of x as x[0] = 5 or x[1] = 2 and so on. The last three statements are not allowed. What does the statement x = 3; mean? As x is a name of array and this statement is not clear, what we are trying to do here? Are we trying to assign 3 to each element of the array? This statement is not clear. Resultantly, it can not be allowed. The statement x = a + b is also not allowed. There is nothing wrong with a + b. But we cannot assign the sum of values of a and b to x. In the statement x = &n, we are trying to assign the memory address of n to x which is not allowed. The reason is the name x is not lvalue and we cannot assign any value to it. For understanding purposes, consider x as a constant. Its name or memory location can not be changed. This is a collective name for six locations. We can access these locations as x[0], x[1] up to x[5]. This is the way arrays are manipulated.
Sometimes, you would like to use an array data structure but may lack the information about the size of the array at compile time. Take the example of telephone directory. You have to store one lakh (100,000) names in an array. But you never know that the number of entries may get double or decline in future. Similarly, you can not say that the total population of the country is one crore (10 million) and declare an array of one crore names. You can use one lakh locations now and remaining will be used as the need arrives. But this is not a good way of using the computer resources. You have declared a very big array while using a very small chunk of it. Thus the remaining space goes waste which can, otherwise, be used by some other programs.
We will see what can be the possible solution of this problem?
Suppose you need an integer array of size n after the execution of the program. We have studied that if it is known at the execution of the program that an array of size 20 or 30 is needed, it is allocated dynamically. The programming statement is as follows:
int* y = new int[20];
It means we are requesting computer to find twenty memory locations. On finding it, the computer will give the address of first location to the programmer which will be stored in y. Arrays locations are contiguous i.e. these are adjacent. These twenty locations will be contiguous, meaning that they will be neighbors to each other. Now y has become an array and we can say y[0] =1 or y[5] = 15. Here y is an lvalue. Being a pointer, it is a variable where we can store the address of some variable. When we said int* y = new int[20]; the new returns the memory address of first of the twenty locations and we store that address into y. As y is a pointer variable so it can be used on the left-hand side. We can write it as:
y = &x[0];
In the above statement, we get the address of the fist location of the array x and store it in y. As y is lvalue, so it can be used on left hand side. This means that the above statement is correct.
y = x;
Similarly, the statement y = x is also correct. x is an array of six elements that holds the address of the first element. But we cannot change this address. However we can get that address and store it in some other variable. As y is a pointer variable and lvalue so the above operation is legal. We have dynamically allocated the memory for the array. This memory, after the use, can be released so that other programs can use it. We can use the delete keyword to release the memory. The syntax is:
delete[ ] y;
We are releasing the memory, making it available for use by other programs. We will not do it in case of x array, as ‘new’ was not used for its creation. So it is not our responsibility to delete x.
Labels: Data Structures
What is programming
As this course is titled “Introduction to programming”, therefore it is most essential and appropriate to understand what programming really means. Let us first see a widely known definition of programming.
Definition: "A program is a precise sequence of steps to solve a particular problem.”
It means that when we say that we have a program, it actually means that we know about a complete set activities to be performed in a particular order. The purpose of these activities is to solve a given problem.
Alan Perlis, a professor at Yale University, says:
"It goes against the grain of modern education to teach children to program. What fun is there in making plans, acquiring discipline in organizing thoughts, devoting attention to detail and learning to be self-critical? "
It is a sarcastic statement about modern education, and it means that the modern education is not developing critical skills like planning, organizing and paying attention to detail. Practically, in our day to day lives we are constantly planning, organizing and paying attention to fine details (if we want our plans to succeed). And it is also fun to do these activities. For example, for a picnic trip we plan where to go, what to wear, what to take for lunch, organize travel details and have a good time while doing so.
When we talk about computer programming then as Mr. Steve Summit puts it
“At its most basic level, programming a computer simply means telling it what to do, and this vapid-sounding definition is not even a joke. There are no other truly fundamental aspects of computer programming; everything else we talk about will simply be the details of a particular, usually artificial, mechanism for telling a computer what to do. Sometimes these mechanisms are chosen because they have been found to be convenient for programmers (people) to use; other times they have been chosen because they're easy for the computer to understand. The first hard thing about programming is to learn, become comfortable with, and accept these artificial mechanisms, whether they make ``sense'' to you or not. “
Goals of this Course
Reinforce the concept that costs and benefits exist for every data structure. We will learn this with practice.
Learn the commonly used data structures. These form a programmer's basic data structure “toolkit”. In the previous course, you have learned how to form a loop, functions, use of arrays, classes and how to write programs for different problems. In this course, you will make use of data structures and have a feeling that there is bag full of different data structures. In case of some problem, you will get a data structure from the toolkit and use some suitable data structure.
Understand how to measure the cost of a data structure or program. These techniques also allow you to judge the merits of new data structures that you or others might develop. At times, you may have two suitable data structures for some problem. These can be tried one by one to adjudge which one is better one. How can you decide which data structure is better than other. Firstly, a programmer can do it by writing two programs using different data structure while solving the same problem. Now execute both data structures. One gives the result before the other. The data structure that gives results first is better than the other one. But sometimes, the data grows too large in the problem. Suppose we want to solve some problem having names and the data of names grows to10 lakhs (one million). Now when you run both programs, the second program runs faster. What does it mean? Is the data structure used in program one not correct? This is not true. The size of the data, being manipulated in the program can grow or shrink. You will also see that some data structures are good for small data while the others may suit to huge data. But the problem is how can we determine that the data in future will increase or decrease. We should have some way to take decision in this regard. In this course we will do some mathematical analysis and see which data structure is better one.
Labels: Data Structures
Data Structure Philosophy
Let’s talk about the philosophy of data structure. Each data structure has costs and benefits. Any data structure used in your program will have some benefits. For this, you have to pay price. That can be computer resources or the time. Also keep in mind that you are solving this problem for some client. If the program is not efficient, the client will not buy it.
In rare cases, a data structure may be better than another one in all situations. It means that you may think that the array is good enough for all the problems. Yet this is not necessary. In different situations, different data structures will be suitable. Sometimes you will realize that two different data structures are suitable for the problem. In such a case, you have to choose the one that is more appropriate. An important skill this course is going to lend to the students is use the data structure according to the situation. You will learn the programming in a way that it will be possible to replace the one data structure with the other one if it does not prove suitable. We will replace the data structure so that the rest of the program is not affected. You will also have to attain this skill as a good programmer.
There are three basic things associated with data structures. A data structure requires:
- space for each data item it stores
- time to perform each basic operation
- programming effort
Reinforce the concept that costs and benefits exist for every data structure. We will learn this with practice.
Learn the commonly used data structures. These form a programmer's basic data structure “toolkit”. In the previous course, you have learned how to form a loop, functions, use of arrays, classes and how to write programs for different problems. In this course, you will make use of data structures and have a feeling that there is bag full of different data structures. In case of some problem, you will get a data structure from the toolkit and use some suitable data structure.
Understand how to measure the cost of a data structure or program. These techniques also allow you to judge the merits of new data structures that you or others might develop. At times, you may have two suitable data structures for some problem. These can be tried one by one to adjudge which one is better one. How can you decide which data structure is better than other. Firstly, a programmer can do it by writing two programs using different data structure while solving the same problem. Now execute both data structures. One gives the result before the other. The data structure that gives results first is better than the other one. But sometimes, the data grows too large in the problem. Suppose we want to solve some problem having names and the data of names grows to10 lakhs (one million). Now when you run both programs, the second program runs faster. What does it mean? Is the data structure used in program one not correct? This is not true. The size of the data, being manipulated in the program can grow or shrink. You will also see that some data structures are good for small data while the others may suit to huge data. But the problem is how can we determine that the data in future will increase or decrease. We should have some way to take decision in this regard. In this course we will do some mathematical analysis and see which data structure is better one.
Labels: Data Structures
Selecting a Data Structure
How can we select the data structure needed to solve a problem? You have already studied where to use array and the size of array and when and where to use the pointers etc. First of all, we have to analyze the problem to determine the resource constraints that a solution must meet. Suppose, the data is so huge i.e. in Gega bytes (GBs) while the disc space available with us is just 200 Mega bytes. This problem can not be solved with programming. Rather, we will have to buy a new disk.
Secondly, it is necessary to determine the basic operations that must be supported. Quantify the resource constraints for each operation. What does it mean? Suppose you have to insert the data in the computer or database and have to search some data item. Let’s take the example of telephone directory. Suppose there are eight million names in the directory. Now someone asks you about the name of some particular person. You want that this query should be answered as soon as possible. You may add or delete some data. It will be advisable to consider all these operations when you select some data structure.
Finally select the data structure that meets these requirements the maximum. Without, sufficient experience, it will be difficult to determine which one is the best data structure. We can get the help from internet, books or from someone whom you know for already getting the problems solved. We may find a similar example and try to use it. After this course, you will be familiar with the data structures and algorithms that are used to solve the computer problems.
Now you have selected the data structure. Suppose a programmer has inserted some data and wants to insert more data. This data will be inserted in the beginning of the existing data, or in the middle or in the end of the data. Let’s talk about the arrays and suppose you have an array of size hundred. Data may be lying in the first fifty locations of this array. Now you have to insert data in the start of this array. What will you do? You have to move the existing data (fifty locations) to the right so that we get space to insert new data. Other way round, there is no space in the start. Suppose you have to insert the data at 25th location. For this purpose, it is better to move the data from 26th to 50th locations; otherwise we will not have space to insert this new data at 25th location.
Now we have to see whether the data can be deleted or not. Suppose you are asked to delete the data at 27th position. How can we do that? What will we do with the space created at 27th position?
Thirdly, is all the data processed in some well-defined order or random access allowed? Again take the example of arrays. We can get the data from 0th position and traverse the array till its 50th position. Suppose we want to get the data, at first from 50th location and then from 13th. It means that there is no order or sequence. We want to access the data randomly. Random access means that we can’t say what will be the next position to get the data or insert the data.
Labels: Data Structures
Introduction to Data Structures
Let’s discuss why we need data structures and what sort of problems can be solved with their use. Data structures help us to organize the data in the computer, resulting in more efficient programs. An efficient program executes faster and helps minimize the usage of resources like memory, disk. Computers are getting more powerful with the passage of time with the increase in CPU speed in GHz, availability of faster network and the maximization of disk space. Therefore people have started solving more and more complex problems. As computer applications are becoming complex, so there is need for more resources. This does not mean that we should buy a new computer to make the application execute faster. Our effort should be to ensue that the solution is achieved with the help of programming, data structures and algorithm.
What does organizing the data mean? It means that the data should be arranged in a way that it is easily accessible. The data is inside the computer and we want to see it. We may also perform some calculations on it. Suppose the data contains some numbers and the programmer wants to calculate the average, standard deviation etc. May be we have a list of names and want to search a particular name in it. To solve such problems, data structures and algorithm are used. Sometimes you may realize that the application is too slow and taking more time. There are chances that it may be due to the data structure used, not due to the CPU speed and memory. We will see such examples. In the assignments, you will also check whether the data structure in the program is beneficial or not. You may have two data structures and try to decide which one is more suitable for the resolution of the problem.
As discussed earlier, a solution is said to be efficient if it solves the problem within its resource constraints. What does it mean? In the computer, we have hard disk, memory and other hardware. Secondly we have time. Suppose you have some program that solves the problem but takes two months. It will be of no use. Usually, you don’t have this much time and cannot wait for two months. Suppose the data is too huge to be stored in disk. Here we have also the problem of resources. This means that we have to write programs considering the resources to achieve some solution as soon as possible. There is always cost associated with these resources. We may need a faster and better CPU which can be purchased. Sometimes, we may need to buy memory. As long as data structures and programs are concerned, you have to invest your own time for this. While working in a company, you will be paid for this. All these requirements including computer, your time and computer time will decide that the solution you have provided is suitable or not. If its advantages are not obtained, then either program or computer is not good.
So the purchase of a faster computer, while studying this course, does not necessarily help us in the resolution of the problem. In the course of “Computer Architecture” you will see how the more efficient solutions can be prepared with the hardware. In this course, we will use the software i.e. data structures, algorithms and the recipes through which the computer problems may be resolved with a faster solution.
Labels: Data Structures
Data Structures
Reading Material
Data Structures and algorithm analysis in C++
Summary
- Introduction to Data Structures
- Selecting a Data Structure
- Data Structure Philosophy
- Goals of this Course
- Array
- List data structure
Following are the goals of this course:
- Prepare the students for (and is a pre-requisite for) the more advanced material students will encounter in later courses.
- Cover well-known data structures such as dynamic arrays, linked lists, stacks, queues, trees and graphs.
- Implement data structures in C++
Labels: Data Structures
KEY DATA COMMUNICATION TERMINOLOGY
- Link: connects adjacent nodes Wires, Cables, Any thing that physically connects two nodes
- Path: end-to-end route within a network
- Circuit: the conduit over which data travels
- Packetzing: dividing messages into fixed-length packets prior to transmission over a network’s communication media
- Routing: determining a message’s path from sending to receiving nodes
- The transmission medium may itself be a network, so route needs to be specified
“A NETWORK is a set of devices (Nodes) connected by Communication Links”
- Node: Can be a Computer, Printer or any other device capable of sending or receiving
- The links connecting Nodes are called COMMUNICATION CHANNELS Networks- Why we need them?
It is often impractical for devices to be directly connected for two major reasons:
- The devices are very far apart. They are expensive to connect just two devices with one in Lahore and other in Islamabad
- Large set of devices would need impractical number of connections e .g. Telephone Lines in the world and all the computers owned by a single organization
- Solution is to connect all devices to a central system known as a NETWORK in which all terminals or computers share the links.
- Two Main Classifications of the Networks
- LANS
- WANS
- Instead of a single large machine being responsible for all aspects of a process ,each separate computer handles a subset of the task
- Example – Project Given as a part of the Course
- Example – Office Work
- Security
the entire system.
- For example : Bank’s ATM
- Distributed Data bases
- For example WWW gives user access to pages stored anywhere on Internet
- Faster Problem Solving
computer working alone
- Security through Redundancy
If one computer's hardware breaks down others cover up
- Collaborative Processing
Labels: Data Communication
BYTE STUFFING
Sometimes the special character (i-e soh and eot) may appear in data and as a part of data
they will be misinterpreted as framing data.
The solution to this problem is Byte stuffing.
In general to distinguish between data being sent and control information such as
frame delimiters network systems arrange for the sending side to change the data slightly
before it is sent because systems usually insert data or bytes to change data for
transmission, the technique is known as Data Stuffing.
There are two types of data stuffing:
• Byte Stuffing
• Bit Stuffing
Byte stuffing refers stuffing with character oriented hardware and bit stuffing
refers to bit oriented hardware.
Byte stuffing translates each reserved byte into two unreserved bytes. For
example: it can use esc as prefix followed by x for soh, y for eot and z for eco.
The receiver then replaces each occurrence of esc x, esc y and esc z by the
corresponding single character. This is shown in figure below:
Labels: Computer Networks
Design Recipe
To design a program properly, we must:
- Analyze a problem statement, typically expressed as a word problem
- Express its essence, abstractly and with examples
- Formulate statements and comments in a precise language
- Evaluate and revise the activities in light of checks and tests
- These skills are useful for anybody
- All assignments in this course should follow the these guidelines
Alan Perlis
“It goes against the grain of modern
education to teach children to program.
What fun is there in making plans,
acquiring discipline in organizing
thoughts, devoting attention to detail
and learning to be self-critical? “
UNIVAC 1 1951
UNIVAC-1. The first commercially successful electronic computer, UNIVAC I, was
also the first general purpose computer - designed to handle both numeric and textual
information. It was designed by J. Presper Eckert and John Mauchly. The
implementation of this machine marked the real beginning of the computer era.
Remington Rand delivered the first UNIVAC machine to the U.S. Bureau of Census in
1951. This machine used magnetic tape for input.
first successful commercial computer
design was derived from the ENIAC (same developers)
first client = U.S. Bureau of the Census
$1 million
48 systems built
Labels: Introduction to Computing
Floppy Disk 1950
Invented at the Imperial University in Tokyo by Yoshiro Nakamats
Labels: Introduction to Computing
PACKETS AND FRAMES
PACKETS:
Packet is a generic term that refers to small block of data. Packet have different
format. Each hardware uses different packet format.
FRAME:
A frame or hardware frame denotes a packet of a specific format on a specific
hardware technology.
FRAME FORMAT:
We need to define a standard format for data to indicate the beginning and end of
the frame. Header and tail are used to frame the data as shown in the figure below.
We see that in the figure soh and eot are used to denote the start of header and end of tail.
FRAMING IN PRACTICE:
In practice there is a disadvantage of overhead. To avoid the no delay between
two frames each frame sends an extra character between block of data.
The framing in practice also has some transmission problems just like:
- Missing eot indicates sending computer crashed.
- Missing soh indicates receiving computer missed beginning of message.
- Bad frame is discarded
Labels: Computer Networks
PACKETS, FRAMES AND ERROR DETECTION
INTRODUCTION:
The previous chapters of data communication described how bits are transmitted
across a physical network using a transmission medium.
This chapter introduces the concept of packets of data rather than bits for
communication.
CONCEPT OF ‘PACKET’:
Network systems divide data in small blocks or junks called packets, which they
send individually. Why we need packets rather than bits? The answer to this question is
because a sender and receiver need to coordinate to detect transmission errors. Also the
individual connection between each pair of computers is not possible. That’s why to
solve these problems shard network connections are made among many workstations.
PROBLEMS WITH SHARING:
The demand of sharing is very high because many computers need to use the shared
networks. In addition to this some applications have large data transfer. In this way they
hold the network for long time. But on the other hand some applications cannot wait so
long. So we need a mechanism for fairness.
SOLUTION FOR FAIRNESS:
To the fairness, the solution is to divide the data into small block or chunks called
‘PACKETS’. Computers take turns to send one packet at a time over the shared
connection.
Because each packet is small so no computer experiences a long delay.
Example:
In the figure one reason for using the packets is illustrated. We see that in a shared
resource when one pair of computer communicates, the other must wait. To understand
the use of packet here, let’s suppose a transmission with packets in the figure.
WITHOUT PACKETS:
A 5MB file transferred across network with 56Kpbs capacity will require 12 minutes.
This means that all that computers will be forced to wait for 12 minutes before initiating
entire file) has been sent.
Suppose file is broken into 1000 byte packets.
Now each packet takes less than 0.2 seconds to transmit. Here other computers must only

Note: - if both files are 5MB long, each now takes 24 minutes to transmit. But if the
second file is 10MB long it sill be transmitted in only 2.8 seconds while 5MB file still
takes roughly 12 minutes.
PACKETS AND TDM:
Dividing data into small packets allow time division multiplexing. In TDM each packet
leaves the source and is switched on the shared communication channel through a
multiplexer. At the destination the packet is switched through a demultiplexer to the
destination.
In the figure this process is illustrated with a multiplexing circuit shown.

Labels: Computer Networks
C language program Lecture 3
This same task can be performed by the following program as well. In this case the video text memory is accessed byte by byte.
unsigned char far *scr=(unsigned char far*)0xb8000000;
void main()
{
*scr=0x56;
*(scr+1)=0x07;
*(scr+2)=0x55;
*(scr+3)=0x70;
}
The next example fills whole of the screen with spaces. This will clear the contents of the screen.
unsigned char far *scr=(unsigned char far*)0xb8000000; //corrected
void main()
{
int i; //instruction added
for (i=0;i<2000;i++) scr="0x20;" scr="scr+2;">void interrup
void interrupt newfunc();
char far *scr=(char far* ) 0xb8000000;
void main()
{
setvect(0x08,newfunc);
}
void interrupt newfunc ()
{
*scr=0x41; //corrected
*(scr+1)=0x07; //corrected
In the above example the timer interrupt is intercepted such that whenever the timer interrupt is invoked (by means of hardware) the memory resident newfunc() is invoked. This function simply displays the ASCII character 0x41 or ‘
Here is another example.
void interrupt (*old)();
void interrupt newfunc();
char far *scr=(char far* ) 0xb8000000;
void main( )
{
old=getvect(0x08);
setvect(0x08,newfunc); //corrected
}
void interrupt newfunc ( )
{
*(scr+j)=‘9’; }
}
(*old)();
}
This program scans through all the bytes of text display memory when int 8 occurs. It once resident will replace all the ‘1’ on the screen by ‘9
The keyboard Interrupt
Keyboard is a hardware device and it makes use of interrupt number 9 for its input operations. Whenever a key is pressed interrupt # 9 occurs. The operating system processes this interrupt in order to process the key pressed. This interrupt usually reads the scan code from the keyboard port and converts it into the appr Lets now experiment on the keyboard interrupt to understand its behavior
Lets now experiment on the keyboard interrupt to understand its behavior
Example
#include
void interrupt newfunc( );
void main( )
{
old = getvect(0x09);
keep(0,1000);
}
void interrupt newfunc ( )
{
(*old)( );
(*old)( );
}
This program simply intercepts the keyboard interrupt and places the address of newint in the IVT. The newint simply invokes the origin
Example
#include
void interrupt (*old)( );
void interrupt newfunc( );
void main( )
{
old = getvect(0x09);
setvect(0x09,newfunc);
}
void interrupt newfunc ( )
{
*scr = 64;
(*old)( );
}
The above program is quite familiar it will just set the caps lock status whenever a key is pressed. In this case the keyboard interrup
Example
void interrupt (*old)( );
void interrupt newfunc( );
char far *scr = (char far* ) 0xB8000000;
void main( )
{
old = getvect(0x09);
setvect(0x09,newfunc);
keep(0,1000);
}
void interrupt newfunc ( )
{ for( j = 0;j <>
void interrupt (*oldTimer)( ); //corrected
void interrupt (*oldKey)( ); //corrected
void interrupt newTimer ( );
void interrupt newKey ( );
char far *scr = (char far* ) 0xB8000000
int i, t = 0, m = 0;
char charscr [4000];
void main( )
{
oldTimer = getvect(8);
oldKey = getvect (9);
setvect (8,newTimer);
setvect (9,newKey);
getch();
getch();
getch();
}
void interrupt newTimer ( )
{
t++;
if ((t >= 182) && (m == 0))
{
In the above example the function Proc1() is invoked. On invocation the register AX contained the value 1234H, the code within the function Proc1() changes the value in AX to FF55H. On return AX will contain the value 1234H if the function have been implemented as a reentrant procedure i.e a reentrant procedure would restore the values in registers their previous value (saved in the stacked) before returning.
C language reentrant procedures save the registers in stack following the order AX, BX, CX, DX, ES, DS, SI, DI, BP on invocation and restores in reverse order before return.
This fact about reentrant procedures can be analysed through following example.
#include
void interrupt *old();
void interrupt newint()
void main ()
{
old = getvect(0x65);
setvect(0x65,newint);
_AX=0xf00f;
geninterrupt(0x65);
a = _AX
printf(“%x”,a);
}
void interrupt newint()
{
_AX=0x1234;
}
Firstly its important to compile this above and all the rest of the examples as .C files and not as .CPP file. It these codes are compiled using .CPP extension then there is no surety that this program could be compiled.
Again int 65H is used for this experiment. The int 65H vector is made to point at the function newint(). Before calling the interrupt 65H value 0xF00F is placed in the AX register. After invocation of int 65H the value of AX register is changed to 0x1234. But after return if the value of AX is checked it will not be 0x1234 rather it will be 0xF00F indicating that the values in registers are saved on invocation and restore before return and also that the interrupt type procedures are reentrant.
Labels: Systems Programming
Transistor – 1947
The first transistor was invented at Bell Laboratories on December 16, 1947 by William
Shockley. This was perhaps the most important electronics event of the 20th century, as
it later made possible the integrated circuit and microprocessor that are the basis of
modern electronics. Prior to the transistor the only alternative to its current regulation
and switching functions (TRANSfer resISTOR) was the vacuum tubes, which could only
be miniaturized to a certain extent, and wasted a lot of energy in the form of heat.
Compared to vacuum tubes, it offered:
smaller size
better reliability
lower power consumption
lower cost
Labels: Introduction to Computing
ENIAC – 1946
ENIAC I (Electrical Numerical Integrator And Calculator). The U.S. military sponsored
their research; they needed a calculating device for writing artillery-firing tables (the
settings used for different weapons under varied conditions for target accuracy).
John Mauchly was the chief consultant and J Presper Eckert was the chief engineer.
Eckert was a graduate student studying at the Moore School when he met John Mauchly
in 1943. It took the team about one year to design the ENIAC and 18 months and
500,000 tax dollars to build it.
The ENIAC contained 17,468 vacuum tubes, along with 70,000 resistors and 10,000
capacitors.
Labels: Introduction to Computing
Harvard Mark 1 – 1943:
Howard Aiken and Grace Hopper designed the MARK series of computers at Harvard
University. The MARK series of computers began with the Mark I in 1944. Imagine a
giant roomful of noisy, clicking metal parts, 55 feet long and 8 feet high. The 5-ton
device contained almost 760,000 separate pieces. Used by the US Navy for gunnery and
ballistic calculations, the Mark I was in operation until 1959.
The computer, controlled by pre-punched paper tape, could carry out addition,
subtraction, multiplication, division and reference to previous results. It had special
subroutines for logarithms and trigonometric functions and used 23 decimal place
numbers. Data was stored and counted mechanically using 3000 decimal storage wheels,
1400 rotary dial switches, and 500 miles of wire. Its electromagnetic relays classified the
machine as a relay computer. All output was displayed on an electric typewriter. By
today's standards, the Mark I was slow, requiring 3-5 seconds for a multiplication
operation
Labels: Introduction to Computing
ABC – 1939
The Atanasoff-Berry Computer was the world's first electronic digital computer. It was
built by John Vincent Atanasoff and Clifford Berry at Iowa State University during 1937-
42. It incorporated several major innovations in computing including the use of binary
arithmetic, regenerative memory, parallel processing, and separation of memory and
computing functions
Labels: Introduction to Computing
Vacuum Tube – 1904
A vacuum tube is just that: a glass tube surrounding a vacuum (an area from which all
gases has been removed). What makes it interesting is that when electrical contacts are
put on the ends, you can get a current to flow though that vacuum.
A British scientist named John A. Fleming made a vacuum tube known today as a diode.
Then the diode was known as a "valve,"
Labels: Introduction to Computing
C language program Lecture 2
Another Example:
#include
void interrupt (*oldint65)( );
setvect(0x65, newint65);
if (( _AH ) == 0) //corrected
{
{
if (( _AH ) == 1) //corrected
}
Various interrupts provide a number of services. The service number is usually placed in the AH register before invoking the interrupt. The ISR should in turn check the value in AH register and then perform the function accordingly. The above example exemplifies just that. In this example int 65 is assigned two services 0 and 1. Service 0 prints the string st and service 1 prints the string st1. These services can be invoked in the following manner.
void main()
{ Fig 2 (The original ISR being called at he end of new routine)
Fig 2 (The original ISR being called at he end of new routine)  Fig 3 (The original ISR invoked at the start of new ISR)
Fig 3 (The original ISR invoked at the start of new ISR) Care must be taken while invoking the original interrupt. Generally in case hardware interrupts are intercepted invoking the original interrupt at the start of new routine might cause some problems whereas in case of software interrupts the original interrupt can be invoked anywhere
Care must be taken while invoking the original interrupt. Generally in case hardware interrupts are intercepted invoking the original interrupt at the start of new routine might cause some problems whereas in case of software interrupts the original interrupt can be invoked anywhere
Sample Program for interrupt Interception
void interrupt newint();
void interrupt (*old)();
void main()
{
old=getvect(0x08);
setvect(0x08,newint);
keep(0,1000);
}
void interrupt newint ()
{
…
…
(*old)();
}
The above program gets the address stored at the vector of interrupt 8 and stores it in the pointer oldint. The address of the interrupt function newint is then placed at the vector of int 8 and the program is made memory resident. From this point onwards whenever interrupt 8 occurs the interrupt function newint is invoked. This function after performing its operation calls the original interrupt 8 whose address has been stored in oldint pointer.
Timer Interrupt
In the coming few examples we will intercept interrupt 8. This is the timer interrupt. The timer interrupt has following properties.
- Its an Hardware Interrupts
- It is Invoked by Means of Hardware
- It approximately occurs 18.2 times every second by means of hardware.
BIOS Data Area
BIOS contains trivial I/O routines which have been programmed into a ROM type device and is interfaced with the processor as a part of main memory. However the BIOS routines would require a few variables, these variables are stored in the BIOS data arera at the location 0040:0000H in the main memory.
One such byte stored in the BIOS data area is the keyboard status byte at the location 40:17H. This contains the status of various keys like alt, shift, caps lock etc. This byte can be described by the diagram below
Fig 4 (Keyboard status byte)

Another Example
#include
void interrupt (*old)();
void main()
old=getvect(0x08);
setvect(0x08,new);
}
*scr=64;
(*old)();
This fairly simple example intercepts the timer interrupt such that whenever the timer interrupt occurs the function new() is invoked. Remember this is .C program and not a .CPP program. Save the code file with .C extension after writing this code
Memory Mapped I/O and Isolated I/O

Fig 6 (Memory mapped I/O)

Memory Mapped I/O on Monitor
One of the devices in standard PCs that perform memory mapped I/O is the display device (Monitor). The output on the monitor is controller by a controller called video controller within the PC. One of the reason for adopting memory mapped I/O for the monitor is that a large amount of data is needed to be conveyed to the video controller in order to describe the text or that graphics that is to be displayed. Such large amount of data being output through isolated I/O does not form into a feasible idea as the number of port in PCs is limited to 65536.
The memory area starting from the address b800:0000H. Two bytes (a word) are reserved for a single character to be displayed in this area. The low byte contains the ASCII code of the character to be displayed and the high byte contains the attribute of the character to be displayed. The address b800:0000h corresponds to the character displayed at the top left corner of the screen, the next word b800:0002 corresponds to the next character on the same row of the text screen and so on as described In the diagram below.
Fig 7 (Memory mapped I/O on monitor)

The attribute byte (higher byte) describes the forecolor and the backcolor in which the character will be displayed. The DOS screen carries black as the backcolor and white as the fore color by default. The lower 4 bits (lower nibble) represents the forecolor and the higher 4 bits (higher nibble) represents the back color as described by the diagram below
Fig 8 (Attribute Byte)
 To understand all describe above lets take a look at this example.
To understand all describe above lets take a look at this example.unsigned int far *scr=0xb8000000;
void main()
{
(*scr)=0x0756;
(*(scr+1))=0x7055;
}
This example will generate the output VU
The far pointer scr is assigned the value 0xb800H in the high word which is the segment address and value 0x0000H in the low word which is the offset address. The word at this address is loaded with the value 0x0756H and the next word is loaded by the value 0x7055H, 0x07 is the attribute byte meaning black back color and white fore color and the byte 0x70h means white back color and black fore color. ).0x56 and 0x55 are the ASCII value of “V” and “U” respectively.
Labels: Systems Programming







